What do you do? You check your email and find a message from your bank threatening to close your account if you don’t reply immediately with your contact information, or an email arrives from a business associate that includes a link to a web site that you don’t recognize. You’ve gotten email from them before, but this one seems suspicious.
These messages and others like them are examples of phishing, a method of online identity theft. In addition to stealing personal and financial data, phishers can infect computers with viruses and convince people to participate in criminal activity.
The cyber attacker’s goal is for you to click on a link. However, instead of harvesting your information, the goal is to infect your computer. If you click on the link, you are directed to a website that silently launches an attack against your browser, and, if successful, these cyber criminals have full control over your computer and possibly your entire network.
Scams
Classic examples of scams meant to defraud you include notices that you’ve won the lottery (even though you never entered it) or that a dignitary needs to transfer millions of dollars into your country and would like to pay you to help with the transfer. They will then tell you that you have to pay a processing fee before you can get your money. After you pay these fees the criminals disappear, never to be heard from again.
How to Protect Yourself
For most phishing attacks to be successful you have to do something after reading the email (such as opening the attachment, clicking on the link, or responding to the request for information). If after reading an email you think it is a phishing attack or scam, simply delete the message. Here are some indications that an email is a phishing attack.
- Be suspicious of any email that requires immediate action or creates a sense of urgency.
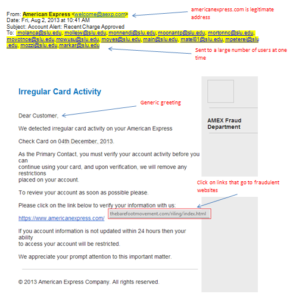
- Be suspicious of emails addressed to “Dear Customer” or some other generic salutation.
- Spelling and bad grammar. Professional companies or organizations usually have a staff of copy editors that will not allow a mass email like this to go out to its users. If you notice mistakes, it might be a scam.
- Beware of links in email. If you see a link in a suspicious email message, don’t click on it. Rest your mouse (but don’t click) on the link to see if the address matches the link that was typed in the message. In the example below the link reveals the real web address, as shown in the box with the yellow background. The string of cryptic numbers looks nothing like the company’s web address.
- Do not click on links. Instead, copy the URL from the email and paste it into your browser. Even better is to simply type the destination name into your browser. For example, if you get an email from UPS telling you your package is ready for delivery, do not click on the link. Instead, go to the UPS website and then copy and paste the tracking number.
- Be suspicious of attachments; only open attachments that you were expecting.
- An email from your friend does not mean they sent it. Your friend’s computer may have been infected or their account may have been compromised, and malware is sending the email to all of your friend’s contacts. If you get a suspicious email from a trusted friend or colleague, call them to confirm that they sent it.
What does a phishing email message look like?
Example 1.
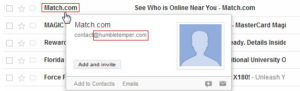
Probably the easiest way to identify if an email is legitimate or not, is to simply hover your mouse arrow over the name in the “From” column. For example, an email from Match.com should typically have the “From” domain of “match.com” (not “humbletemper.com”).
Example 2.
Example 3.

Please follow this link to view more examples of phishing emails:
http://www.phishing.org/phishing-examples
Ultimately, using email safely is all about common sense. No legitimate business or organization will ever ask for your password or personal information. If something seems suspicious or too good to be true, it is most likely a phishing attempt. Simply delete the email.
Resource links:
https://www.securingthehuman.org/newsletters/ouch/issues/OUCH-201112_en.pdf
https://en.wikipedia.org/wiki/Phishing#Helping_to_identify_legitimate_websites
